Unless you have been living under a rock for the past few months, you must have heard about the Ashley Madison account hack. This was where hackers released the entire user database of names, email addresses, billing information, and account details of 38 million users tied to the site. Some described the historical hack episode as an extinction-level event for privacy.
Attack Aftermath
We were shocked when we first learned that hackers managed to steal close to 40 million users’ records from Ashley Madison, which made claims shortly after the incident that its members remained anonymous. Continue reading...

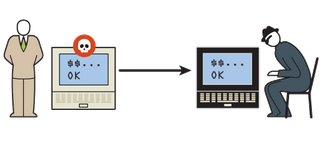 To infiltrate your bank account hackers need exactly the same set of complete credentials you would supply to your online banking site. It is extremely rare, although not impossible, that a hacker would directly contact someone who would then voluntarily give away her bank account number, login name, and password over the phone or email. But it is very common that a compromised PC infested with malware can provide hackers with the necessary recorded keystrokes, mouse clicks, and even screenshots. By mimicking the procedures they’ve learned with the obtained credentials, hackers can digitally impersonate you and thus gain access to your bank accounts over the Internet with ease.
To infiltrate your bank account hackers need exactly the same set of complete credentials you would supply to your online banking site. It is extremely rare, although not impossible, that a hacker would directly contact someone who would then voluntarily give away her bank account number, login name, and password over the phone or email. But it is very common that a compromised PC infested with malware can provide hackers with the necessary recorded keystrokes, mouse clicks, and even screenshots. By mimicking the procedures they’ve learned with the obtained credentials, hackers can digitally impersonate you and thus gain access to your bank accounts over the Internet with ease.