We’ll begin with a definition of what a firewall is and then move into some basic questions and answers. After that we’re going to provide information for those that might want to beef up their firewall protection.
The Firewall Basics
Effectively a firewall is a filter. It is designed to prevent dubious programs and Internet services from establishing a connection or gaining access to your computer.
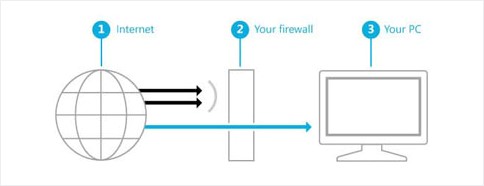
Firewall Defined: A firewall is hardware or software technology designed to monitor and filter incoming and outgoing traffic to your PC. It is a network security function that effectively acts as a barrier. The data that passes through depends on the pre-determined set of rules which are configured in the firewall settings.
A Little Q and A
Now that we know basically what it is, we can answer some questions.
- Why do I need one?
A firewall tries to screen out incoming Internet streams of data from unwanted sources and it also prevents programs on your PC to access the Internet without authorization. The purpose is to prevent unwanted and malicious programs from communicating to, or from, your computer.
- Who makes firewalls?
Microsoft includes a firewall with Windows – we’ll cover this in more detail below. There are also a significant number of known makers of free and paid solutions. The best known names would include Norton, McAfee, BitDefender, Kaspersky, as well as Zone Alarm, Webroot, and Comodo. Some routers also have firewalls built into them. While we are not recommending any specific option, selecting one of the manufacturers listed above should provide greater security.
- When do I need one?
Quite simply – you need a firewall when you connect to the Internet. This is why you should also consider a solution for your smart phone or mobile device. Most malware programs these days attempt to get money from you and your mobile devices are also targets of malware attacks and cyber crime.
- Doesn’t Windows already come with a firewall?
Yes, it does, and it may be all you need. It blocks unwanted connections and will prompt you if you want to allow a connection or not. There is a list of programs to block and you can enter exceptions to identify programs you deem safe.
Windows Firewall is equipped to monitor traffic, but lacks in the area of program control. Despite shortcomings, Windows Firewall may be all you need. Other tools will provide additional functions such as the ability to create activity logs. In this way you can review what was happening in terms of attempted connections so you can fine tune the security parameters. The bottom line is that the Windows Firewall will suffice for most users and should not be regarded as providing insufficient security.
If you find surfing the net is slow, begin by optimizing the browsers and Windows configuration for accessing the Internet. We recommend looking at the articles: Improve Internet Speed and Restore Browser Speed. After this, if you are more certain that the firewall is affecting performance, you may want to replace it. If your PC is encountering issues with viral infections then first look at your antivirus protection, and if you have a top notch AV solution and are still getting breaches, that too would be a reason for looking for a new firewall.
- Is a firewall all the protection I need?
In a previous article we covered some myths about antivirus protection and this came up. We can review briefly here. As we have described, firewalls can filter nefarious traffic. However, they cannot protect your PC from files that contain a virus or Trojan. The reason for this is that firewalls are not able to scan for infected files – you need an antivirus solution specific to this purpose.
Cyber criminals exploit potential security holes and look for ways to openly connect with your PC. A firewall can minimize this risk and offer the first line of defense. However, it is not sufficient in blocking the myriad of virus and malware threats that are prevalent. Malware creators are very clever in disguising data and can even disable your firewall in an effort to steal private or personal data.
Antivirus Protection:In a nutshell… we are pleased to offer CompuClever Antivirus PLUS, an AV solution that delivers 100% protection against both known and unknown viruses, comparable to any first-tier antivirus software like Norton, Kaspersky, Bitdefender, and MacAfee. As a matter of fact, an independent third-party lab test revealed that our antivirus product not only delivers a high level of protection, it also creates a very low impact to PC performance.
For more information about CompuClever Antivirus PLUS click here: Are You Well Protected?
Turning Windows Firewall On and Off
Microsoft states: “You only need one firewall app on your PC (in addition to the firewall that’s probably built into your network router). Having more than one firewall app on your PC can cause conflicts and problems.” [1] It is also good practice to NOT turn off a firewall unless you have another one turned on.
With these safe practices in mind, you can view the status of Windows Firewall and you can turn it off or on. The easiest way to begin is to type “firewall” in the Search field located in the Start menu. For more information and instructions specific to your operating system follow one of these links:
Windows 10 / Windows 8 / Windows 7 / Windows Vista / Windows XP
What to Consider if Seeking an Alternative
Here is our list to help you better decide on alternatives to the built-in firewall for Windows.
- You need to consider how accurately a firewall solution will identify threats to your system. You do not want it to miss threats but you also do not want it blackball safe and known programs. No one wants an unending stream of warnings from their firewall for no valid reason. The very best firewalls handle unknown programs by monitoring them closely for suspicious activity and signs of improper network activity behaviour.
- The fewer resources it requires the better. This will allow your system to run programs faster and dedicate resources to perform duties related to regular day-to-day activities.
- Supply only the functions you need. Some “suite” applications will include antivirus and performance tools. If you already have these areas covered by other applications there is no need to pay for bloated software that is inadequate in these other areas.
- You will also need to know what kind of coverage you require in terms of the devices you are needing to protect (desktop, laptop, tablet, or phone), and if your solution will suffice.
Other Considerations
Now to finish off with some final points related to installing a new firewall solution.
Install Your Firewall
There isn’t any one “right” place to install a firewall; it comes down to the devices you use and the programs you run. If you are looking for a firewall for your business then the normal firewall is not what you need; you need what is known as a “Next Generation Firewall” or, “NGFW’. These are more sophisticated and expensive, ranging from $500 to $80,000, and are beyond what we will discuss here.
Also, some routers have firewalls built right into them, meaning any system behind them does not need a firewall. This is useful as it means that there is no performance loss for Windows as a result of a firewall performing checks on data streams. However, if you have a portable device (like a laptop, tablet, or phone), then you need a firewall installed to the device that can be turned on whenever you connect to the Internet when away from home.
Common Problems
The most common problem in using a firewall is blocking a program you know is good. When this happens you need to create an “exclusion” or “exception” (search the program help files for those terms). Effectively, this provides you the ability to override what the firewall would normally do. Firewalls are designed to run in the background so most people have little to no interaction with these programs once they are installed and exceptions are generated.
Summary
While we haven’t gone into detail about hardware and software firewall technologies and the various viral threats to firewalls, we have covered the basics. Standard coverage should get you started and you have the option of customizing the onboard Windows Firewall. As an alternative to Windows, you can follow our introductory guidelines for taking on an alternative firewall solution. In either event, remember that an effective antivirus solution is part of your fortress of protection.
We would like to thank Richard from our Tech Support team for his first wave of research on this subject. We will continue to provide story lines like this and we will describe them in a manner that is within reach of everyday computer users. If you have some ideas of topics you would like us to cover, email us at: newsletter@compuclever.com