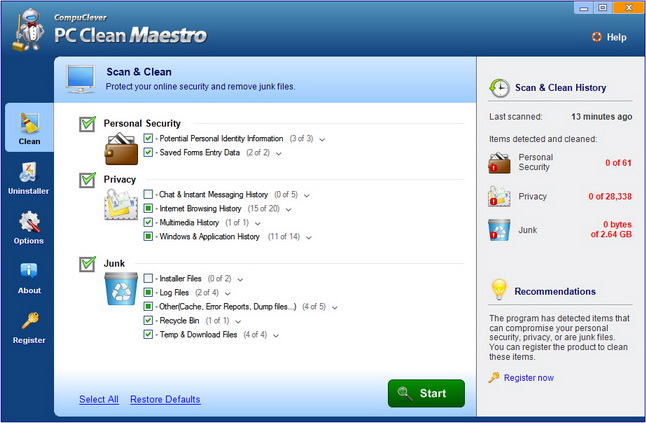
Making a Decision That Works for You:
 Before you begin using a cloud storage provider, it is best to consider the determining factors. Here are a few of the items to consider.
Before you begin using a cloud storage provider, it is best to consider the determining factors. Here are a few of the items to consider.
Cost: Many storage providers will offer an entry level for free. You can then upgrade to a larger storage package based on various levels of cost. Some subscription levels will also get you very large amounts of storage or even unlimited storage and perhaps more functionality (as would be the case if you want an enterprise subscription). For entry level users we suggest free. When you compare you will want to pay close attention to whether it is a monthly or annual payment plan.
Storage Size: If you are going to be using cloud storage for the purpose of sharing files and accessing files via mobile devices, you will not likely need a lot of space. As most providers offer 2 to 5 GB of space for free this will likely work for you. However, if you are considering backing up all your files or if you have a considerable amount of multi-media files to backup, you will need to take inventory of how much space you are currently using for these files. If you have little experience about file size, we suggest you see the “Space It Out” section below to get an idea of file space needs.
Access: Most providers will work if you are using a Windows operating system or Mac. If you are using Linux then you will want to pay closer attention to what options are available. This is also true if you want to access your files from a mobile device such as from Android, Blackberry, or iOS. Dropbox for instance supports all of these platforms.
Sharing, Backup, or Both: This factor relates to the prime reason for using online storage. If you want to share files easily then the most basic levels of cloud storage will work for you (that is, something free with 2 to 5 GB of storage). If you decide that this form of online storage meets your needs, then you would want more storage and begin looking for a payment plan that works for you.
Recommendations:
We do not have any affiliation to the companies we recommend nor do we benefit from our recommendations. We feel free to pass on our experiences when the use of a given solution is considerably beneficial. Our recommendations with respect to cloud storage use:
- We recommend that you do not rely solely on cloud storage as a means of backing up your data. We suggest instead that you use a combination of your PC, external hard drive, and online storage. While keeping in mind that all hard drives will eventually fail, it is a safe bet to have data on more than one device as simultaneous failure is very unlikely. This way you will have the best of all worlds… being able to back up your important files, share any files via the cloud to others, access file on your own mobile devices, and feel secure in the knowledge that your data is safe from the most common forms of loss.
- If you are using an external hard drive you will need to synchronize your files periodically. We suggest trying out Microsoft’s Sync Toy. This free tool makes synchronizing your files fast and easy. You can avoid duplication and feel assured that you haven’t missed backing up all your files.
The Solution:
Now that we have made some recommendations on cloud storage use, we can proceed in helping you get started by by answering some basic questions and coming up with a cloud storage provider that is safe and meets the requirements.
Free: We like free. However it is best to check out what exactly free is. Some companies are able to provide free services through the use of advertisements. Most frequently the provider will charge you once you have exceeded the storage capacity. These companies also stand to profit by converting you to a paid level of subscription usually through a monthly fee. As we have stated in our newsletter article, free is not always free. We see constant prompts to purchase as incurring a cost. This is called “nagware” and is very annoying to contend with. We advise looking closely at the storage solution and examining what they consider to be free. You can check customer reviews for an indication of nagware as you will not see it coming beforehand. Free should also be without any time restrictions.
Space it Out: For you to determine how much space you need you will have to assess what kinds of files you want to store in the cloud. There are several types of file types with varying sizes. So how many files can you store with 2 Giga Bytes (GB) of space? The answer… it depends (of course). Here is a way of thinking about it:
| File Type: | Average Size: | # of files (for 2 GB of storage): |
| Word Document: | 15 KB per page | 69,905 (2 page documents) |
| Emails: | 10 KB | 209,715 |
| MP3: | 3.5MB | 585 |
| Image (TIFF) | 65 KB | 32,263 |
| E-Book | 1-5 MB | 410 – 2048 |
Note: For images… the range of file size is considerably variable based on compression and quality of photo as well as the type of format used (compressed JPG format compared to lossless TIFF or GIF files). These examples are to provide a way of wrapping your head around how much space you require. We have not included movie files here as they are typically close to 1 GB and can go upwards for high definition movies. It is not advisable to store movies using cloud storage as upload times are slow, storage space is at a premium, and some providers place limits on file size.
Multi-platform: We prefer to have a system whereby it does not matter if you access files via your PC, a Mac, or a mobile device. The other consideration is some providers (like Google Docs), have a web client interface where multiple users can edit a file. However, once you attempt to use this file with your computer software you have formatting issues. In effect it becomes only a working file.
The Choice – Dropbox: Given that the other options are likely similar between these providers (web interfacing and integration with Windows Explorer), we recommend Dropbox. It offers 2 GB of free space with no time restrictions or nags, you can get more storage for free (as we outline below), it sets up very well with Windows Explorer, and it has very good cross platform support (for example, Windows, Mac OS X, iOS, and Android) so you can synchronize between computers and devices.
Get Started with DropBox:
We are going to outline how to get started, how to get more storage space while maintain the free entry level, how to interact with Windows Explorer, uploading and downloading via your web browser, and how you can recover files that you accidentally deleted. To begin, you will need to first set up an account. Instruction 1 – Getting Started: Here are the steps to downloading and creating Dropbox:
- Open a web browser and go to the Dropbox.com website.
- Click the Download Dropbox button.
- Click Run to begin the download.
- Once downloaded click Run.
- Click Install.
- Select “I don’t have a Dropbox account” and click Next.
- Fill out your account information (name, email, password) and click Next.
- You can now select the size of Dropbox you want to create. Confirm the 2 GB free option is selected and click Next.
- Choose either the Typical or Advanced setup (to choose custom options), and click Next.
- You can go through the tour or skip the tour and see it later to gain more storage space for free.
When you are done, a Dropbox folder is created on your computer.
Instruction 2 – On Your Computer:
You now have Dropbox on your computer and you will be able to interact with the files there like any other folder with files. Any time you want to interact with your Dropbox folder we suggest the following:
Your Dropbox folder opens up and you can interact with all the files there as you would if they were stored on your computer. Simply drag and drop files to upload them.
Instruction 3 – Sharing: To share a file or folder you can simply locate it on your computer hard drive, right-click the item and select “Share Dropbox link”. Dropbox provides you with two sub-folders to get you started: Public and Photos. Let’s take a look at instructions on how to share photos as provided by Dropbox. With the Dropbox photo galleries you can share photos with anyone including non-Dropbox users. These photos are available in a photo gallery that is viewable online.![]()
- Make a folder inside the Photos folder, and give it a name (this will be the name of your photo gallery).
- Put photos inside the folder you just created (drag and drop them there).
You can easily share a folder by right-clicking and selecting “Share this folder”. That’s it! You can view this photo gallery online by going to: www.dropbox.com/photos.
Instruction 4 – Web Interfacing: You can go to someone else’s computer and access your files. The way to do this is to open a web browser and go to Dropbox.com . Log on using your account information. You can now view your files, share them, or you can download or upload them.
Instruction 5 – Get Space: As mentioned, you begin with 2 GB of free space. There is an incentive program available to increase your storage up to a maximum of 18 GB. For example, if you refer a friend to Dropbox you earn 500 MB of space. Taking a tour is a good idea. You can learn about Dropbox and earn 250 MB of space. For more information on this see: Dropbox.com/getspace.
Instruction 6 – Recover a file: Dropbox uses a feature called “Packrat”. Every change made in your Dropbox folder over a 30 day period is preserved. If you accidentally delete, lose, or erase a file you can recover it using the Packrat feature. Here’s how:
- Open your web browser to the Dropbox.com website.
- Click the “Show deleted files” icon located at the top right of the page (it looks like a trash can with the lid off).
- Deleted files will show up in gray. Select the file you want to recover and click the Restore link.
For more information on how to use Dropbox, go to: Dropbox.com/help.





 Cybercrime has been a growing concern since the onset of the first computer virus. The very first PC threats were more about status and cyber geeks flexing their brain muscle as they penetrate computer defenses and proliferate in typical virus fashion. These days there is much more to lose. Personal information and finances can be stolen with the use of more sophisticated and stealthy technology. One recent hot topics in this field is “skimming wallets” – theft which involves just walking past someone and picking up there credit card information. We will look at this and other forms of cybercrime and speak to how to guard yourself from PC cyber attacks.
Cybercrime has been a growing concern since the onset of the first computer virus. The very first PC threats were more about status and cyber geeks flexing their brain muscle as they penetrate computer defenses and proliferate in typical virus fashion. These days there is much more to lose. Personal information and finances can be stolen with the use of more sophisticated and stealthy technology. One recent hot topics in this field is “skimming wallets” – theft which involves just walking past someone and picking up there credit card information. We will look at this and other forms of cybercrime and speak to how to guard yourself from PC cyber attacks.