Feeling connected is fundamental to the human experience – feeling part of the whole. What better way to do that then from the privacy of our home? We pick and choose when and where and for how long we want to connect when using online social media.
In a previous article we examined Facebook and pointed out its allure. We listed the aspects of this “free” service and we identified “Likes” and “Dislikes”. Were we too quick to accept at face value, the company’s emphasis on the importance of privacy?
A Bit about Facebook
- Facebook, launched in 2004, is the most popular online social media and social networking service. It is based in the U.S. and is the creation of Mark Zuckerberg and his fellow Harvard friends and roommates.
- As of June 2017, Facebook reached 2 billion active users.
- It is a giant in terms of net worth. According to Wikipedia, as of Mar 25, 2018, it is worth US$62.2 billion.
- Recently the company has faced considerable scrutiny and public pressure in relation to hate speech, fake news, depictions of violence, and privacy.
Recent News
Facebook has been in the news multiple times of late. With news related to privacy of data, we need to start with Aleksandr Kogan, a University of Cambridge professor, who created a survey filled out by 270,000 people. In doing so, he was able to access the data of what was reported as more than 50 million Facebook users – recent news has been released whereby Facebook has admitted that upwards of 87 million people were affected by this breach.[1]
While Kogan gained access to this information using legitimate means, via proper channels governing all developers on Facebook, he violated rules related to passing the data to third parties which included Cambridge Analytica.
Zuckerberg was aware of this in 2015. The action taken at that time was to ban Kogan’s app and demand legal certification from Kogan and others he shared it with. According to Zuckerberg[2], Cambridge Analtyica completed certification and told Facebook that they actually hadn’t received raw Facebook data at all. Furthermore, Cambridge Analytica deleted it and weren’t using it.
This reliance on certification turned out to be, as Zuckerberg admits, one of the biggest mistakes made.
Cambridge Analytica: Is a British political consulting firm established in 2013, that combines data mining, data brokerage, and data analysis along with strategic communication. They are in part owned by Robert Mercer and Alexander Nix has been the CEO however, this position was suspended after a Channel 4 news segment was broadcasted. In this he was videotaped in an undercover, hidden camera video interview during which he spoke to someone he believed would use the firm in Sri Lanka for election persuasion purposes. Nix speaks of creating sex scandals and using fake news to manipulate voters.
Cambridge Analytica has been involved in elections worldwide. Their executives claim the company has worked in more than 200 elections around the world, including Nigeria, Kenya, the Czech Republic, India, and Argentina.
In 2016 they became involved in the 2016 Brexit referendum by supporting persuadable voters to vote for leaving the EU. On 18 May 2017, the US Congress began investigation with their connection to Russian attempts to interfere with the 2016 U.S. presidential election. Cambridge Analytica worked for Donald Trump’s political campaign but there is some question as to the level of involvement.[3]
Nix has made bold claims and it is uncertain if some statements have been embellished. He was quoted as saying this in October, 2016:
Today in the United States we have somewhere close to four or five thousand data points on every individual … So we model the personality of every adult across the United States, some 230 million people. [4]
The Data
News reports point to unethical organizations making use of personal data made available by Facebook. This begs the question: what data do they have on us and how can they use it?
Data In:
As soon as a user signs up, data and information is collected. This includes all data – conversations, pictures, videos, and even documents sent via Messenger. Does this surprise you? Would you want to see what the information on you includes?
Should we be concerned? If you use Facebook on your phone and your phone is an Android device, or you use Messenger to send attachments… it would be a good idea to take a closer look.
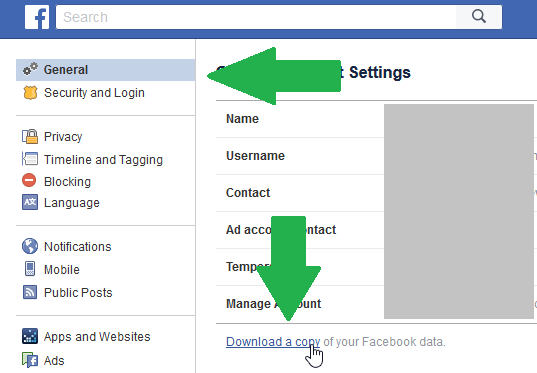
Users are discovering that they can request to have all of their Facebook data in a zip file. Some are astonished to find that this data can include data on every call made and text sent. There are users that are discovering that the data held by Facebook includes rental property lease forms, tenant ledger reports, bill statements, and screen shots of bank transfers.[5]
- Click the down-pointing triangle at the top right of any Facebook page and select Settings
- Click Download a copy of your Facebook data at the bottom of General Account Settings
- Click Start My Archive
In about 10 minutes Facebook processes the request and you’ll get an email and notification when the file is ready to download.
Data Out:
Likely no one is surprised to know that our personal data is being used and shared out to advertisers. Facebook makes money on sharing out data to advertisers and to app developers. The challenge is that there is no control of how the data is used once passed to these groups.
Indeed the most alarming aspect of Cambridge Analytica’s “breach” is that it wasn’t a breach at all. It happened almost entirely above board and in line with Facebook policy.[6]
World Response
Investigations are ramping up world-wide.
US: Zuckerberg will testify before Congress. On April 10, before a joint hearing of the Senate Commerce and Judiciary Committees and the next day before the House Energy and Commerce Committee. The U.S. Federal Trade Commission are conducting separate investigations. [7]
This is a serious matter as stated by Senator Amy Klobuchar who serves on the Senate Judiciary Committee. The senator will ask him to explain “what Facebook knew about misusing data from 50 million Americans in order to target political advertising and manipulate voters.” [8]
UK: Damian Collins, chair for the Digital, Culture, Media and Sport Committee in the House of Commons, questions Facebook user data policies. “Their answers have consistently understated this risk, and have also been misleading to the Committee,” Collins said. “I will be writing to Mark Zuckerberg asking that either he, or another senior executive from the company, appear to give evidence in front of the Committee as part our inquiry.” [9]
MPs on the digital, culture, media and sport committee have accused Facebook of misleading it in a previous evidence session and called for Mark Zuckerberg to appear before them to answer questions. They have also recalled Nix. [10]
A U.K. parliamentary media committee summoned CEO Mark Zuckerberg to testify about how Facebook uses data. U.K. Information Commissioner Elizabeth Denham is investigating how Cambridge Analytica got the data. [11]
Germany: After a meeting with its executives about the abuse of users’ data, the justice minister of Germany stated she wants closer oversight.
Australia: The Information and Privacy Commission has demanded that Facebook provide information on whether any Australian citizens were affected by unauthorized use of profile data. [12]
The Response: Zuckerberg is set to testify next week before a U.S. congressional committee, and he said top executives at the company would be dispatched to other countries wanting to hold government hearings on the scandal. [13]
User Response
Zuckerberg has stated that the users affected by the misuse of personal data by Cambridge Analytica will be notified. To date, this has not yet happened. There are users that are going to delete Facebook as a result of this news and one of the questions we have posed has been: What is the best course of action with regard to Facebook and social media services?
We invite you to give this some thought and to check in with us next week for our Part 2 edition as we outline what Facebook is doing to correct this wrong and we identify the costs associated with what we thought was a “free” service.
We’ll provide out best practices and recommendations for being active on a social media service like Facebook. However, we’ll leave it up to you to choose your level of exposure and if posting online personal information is worth the associated costs.
This concludes the first part of our Facebook and Privacy article.
We’ll pick it up next week. Stay tuned!
[1] https://www.ctvnews.ca/
[2] https://www.wired.com/
[3] https://en.wikipedia.org/
[4] https://news.sky.com/
[5] http://www.nzherald.co.nz/
[6] http://money.cnn.com/2018/03/19/
[7] https://www.ctvnews.ca/
[8] http://money.cnn.com/2018/03/19/
[9] https://www.parliament.uk/business/committees/
[10] https://www.theguardian.com/uk-news/2018/mar/22/
[11] https://www.ctvnews.ca/business/
[12] https://www.theguardian.com/uk-news/2018/mar/22/
[13] http://www.metronews.ca/life/2018/04/04/

 To download your information:
To download your information: