To reverse the impact of foistware on your PC, you need to do the following:
2. Restore changes to your PC made by foistware items, especially to your web browsers.
Removal
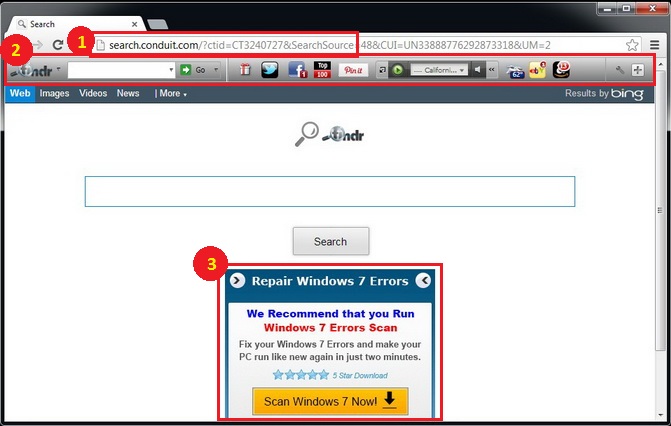
One of the most noticeable effects of foistware is having one or more applications installed. Most of these applications nag you to acquire and/or pay for extra software or services. For example, the 24×7 PC support foistware installs itself to your PC, nags you by attaching itself to every active Window, and shows signs of reluctance when you go to uninstall it.
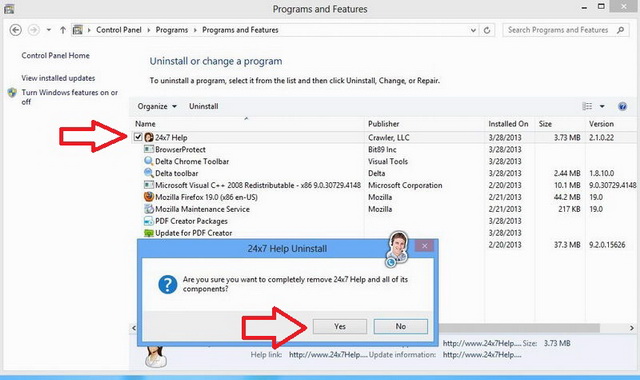
The first step is to remove any application installed by a foistware. To do this we will focus on using the Uninstaller, one of the major tools available with PC Clean Maestro which is free to use. Our previous article covers in detail how to use the Uninstaller. The article also covers other important information such as backing up your system and using the Clean tool. With PC Clean Maestro you can also remove junk files and uninstall programs. You get the added benefit of freeing up space by ridding yourself of “clutter” which can bog down the system and lead to poor system performance. Please refer to the full article: The Clean and Uninstaller Tools.
Removing foistware item is the first step. The next step is restoring your PC. Many anti-virus software tools detect and remove these items but do not restore your PC to its previous settings.
Restore
If you have experienced slower performance in your web browser and changes that occur all of a sudden such as having a different and unknown search engine or homepage, then it is likely you have been subject to foistware. Typically in these situations your web browser settings have been modified without your consent. There are multiple causes of altered web browser settings including installation of browser adware and hijackers program as well as simple misconfiguration as a result of a manual change. The consequence always include poor user experience and often slower web browsing speed.

You can use anti-virus software to remove virus, adware, and hijackers. However, most often security software applications don’t go the extra step – restoring your web browser settings. We provide this guide to show you how you can re-gain control of your web browser by restoring all important settings. Follow this link for more information and instructions:
This guide covers complete sets of instructions for restoring three most popular web browsers: Internet Explorer, Firefox, and Chrome.