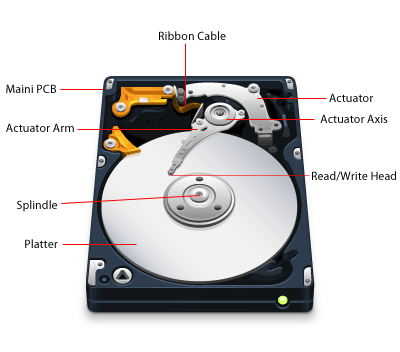
The Hard Disk Drive (HDD) is the main storage device for your PC; it is the mechanism that writes and reads data on the hard disk. The HDD components consist of one or more drive platters sealed within a casing. These drives connect to the motherboard of the computer through the use of internal data transfer and power cables.
The components within the drive include:
- Head Actuator: controls the actuator arm.
- Read/Write Actuator Arm: is similar to the arm of a record player; as the platter is spinning the arm locates and accesses the data needed so it can be read, written (edited), and deleted.
- Read/Write Head: this is the device at the end of the actuator arm and is used to write or read the data on the platter.
- Spindle: holds the platter in place.
- Platter: one or more disks (aluminum, glass, or ceramic) that stores the data. These are coated with a magnetic media and platters rotate at various rotations per minute based on the model of the Hard Disk Drive.
Another critical component is the Disk Controller which contains the necessary instructions for the drive.
Here’s How It Works: Data is transferred to and from the HDD and interpreted by the Disk Controller which acts like the conductor as it instructs the hard drive in terms of what to do and how the internal components needs to function. When you instruct your PC to read or write data, the operating system examines the hard drives’ File Allocation Table (FAT) to examine the available space and location. Once the space is identified, the Disk Controller gives instruction to the Read/Write Actuator Arm and to align the Read/Write Head. Files are often spread out in different areas and the Read/Write Head needs to travel to each location to access the required data.
 In this process, the data is stored magnetically like how a cassette tape works. In fact, both use the same recording techniques. The magnetic medium can be erased and re-written easily. If your PC needs data it would read the magnetic polarities on the platter. One side is a “0” and the other a “1” – this is referred to as binary data. Unlike cassette tapes, the Read/Write Head never touches the disk and consumer PC platters typically spin at 7,200 rpm; a speed of up to 3,000 inches per second. Also, much more information can be read to a disk in much smaller space than cassettes. Both speed and precision account for the ability to record so much data in such small magnetic domains.
In this process, the data is stored magnetically like how a cassette tape works. In fact, both use the same recording techniques. The magnetic medium can be erased and re-written easily. If your PC needs data it would read the magnetic polarities on the platter. One side is a “0” and the other a “1” – this is referred to as binary data. Unlike cassette tapes, the Read/Write Head never touches the disk and consumer PC platters typically spin at 7,200 rpm; a speed of up to 3,000 inches per second. Also, much more information can be read to a disk in much smaller space than cassettes. Both speed and precision account for the ability to record so much data in such small magnetic domains.
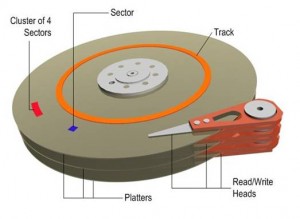
The Platter: The data that is written onto the platter is stored in tracks and sectors. A track is a concentric circle on the platter and a sector is a wedge, a pie-shaped section on the platter. Where these two shapes intersect is a single section on a single track which is known as a “track sector”. File systems, which work to organize these massive amounts of data, will organize groups of sectors into clusters. These terms are useful to familiarize yourself with when looking at the process of fragmentation.
Fragmentation
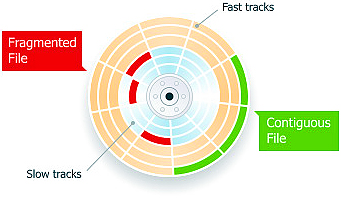
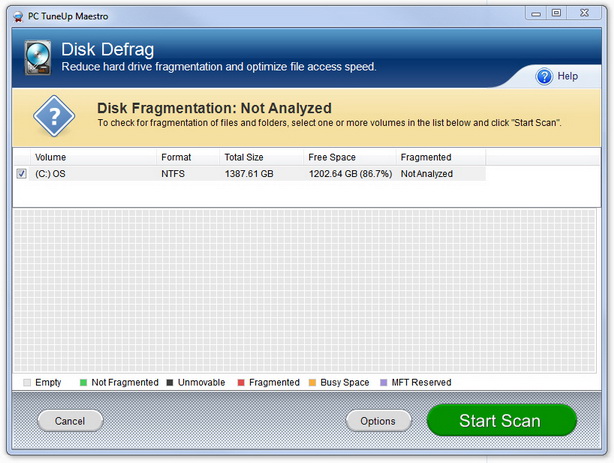
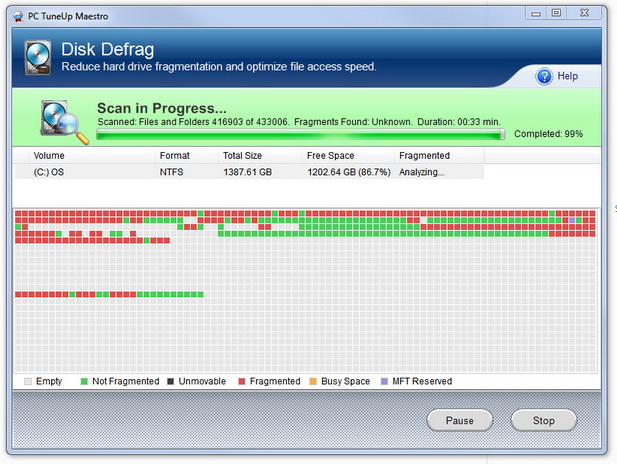
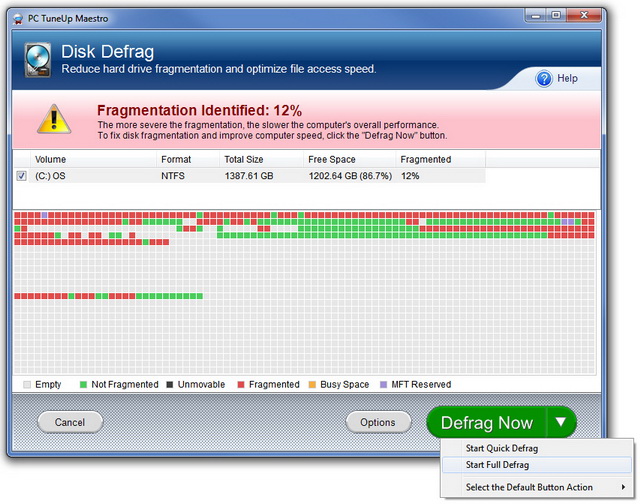
Disk fragmentation is a condition which occurs when files are stored in scattered sections throughout the disk. This occurs as a result of frequently creating, deleting, and modifying files. The operating system uses what free space is available including those areas of the disk that become available when items are moved or deleted. When files do not fit exactly they are broken into pieces; into non-contiguous clusters. Working with large files and numerous files can exacerbate this condition. One of the negative results of this is performance degradation.
How it happens: Storing new data, deleting data, and making modifications to files are all normal day-to-day occurrences with PC use. Disk fragmentation occurs over time as a result of these activities. Here is an example. You download a Word document from email. It is stored in available free space on your disk. Each time you make a change to the file and save the changes, the data is stored in a location different from the original. Further revisions to the file are again stored in different locations. Not only is the disk fragmented over time, so are the files that are modified in this way. The PC has to search for these fragments in different places and as a result the computer performance is slower than what it could be if the files were stored in a sequential fashion.
In other cases one file may be written to the disk in numerous places of the disk as a result of the size of the file or the available space on the disk. Also, groups of files that are needed to be read sequentially (audio/visual gaming media, resource files for an application, and more) are often stored in a non-contiguous or fragmented order. Over time even files that are stored in a contiguous fashion may become fragmented as some files are deleted or updates are made. In these cases files that are unrelated are filled into the gaps that are created. Many of the modern systems on the market today suffer less from fragmentation due to the size of the disk with respect to capacity. If there is considerable free space available, fragmentation is less likely to be as severe.
Summary
Fragmentation occurs with regular PC use. While some activities such as installing / uninstalling large applications and media files can result in more rapid fragmentation, gradual fragmentation can occur from online surfing and the use of office applications.
To learn how a performance degrades when a PC experiences fragmentation and be proactive with regular defragmentation that suites your computing day-to-day use, read the following articles:

 Hard Disk Drive (HDD) performance is measured in the following manners:
Hard Disk Drive (HDD) performance is measured in the following manners: