There are many online references providing information and instruction on cleaning junk files and cleaning your PC. Many of these articles offer instructions on how to go about manually using the onboard tools supplied by your PC operating system. The difficulty with this is:
- Much of this depends on what operating system you are running.
- This can be time consuming if you do not know where these Microsoft tools are located.
- Manual removal of files is almost always tedious and does not produce thorough results as items are stored by programs in areas without your awareness.
- Quite often you need a fair bit of PC expertise and a whole lot of patience.
What you are basically being told to do is to locate some tool which would depend on what OS you are running (for example, there is the “Add or Remove Programs” tool for XP and the “Program and Features” tool in Windows 7). Then you can locate and delete items one by one. Some of these instructions can be challenging for some. For example: “Delete the contents of the “Windows/Temp” folder located in the root directory of the hard drive”. Even if you complete on this task it is incomplete as the items are placed in the Recycle bin.
Some of the instructions that we have come across even include inserting the Windows installation disk and reinstalling the operating system. This is a major undertaking and should only be done after thorough backing up of programs and files and when all other attempts have failed. Typically this would mean there is something even more wrong with your system such as having a computer malware or PC viral infection that cannot be easily removed. What we are looking at though is something more common and less desperate – a gradual PC performance slow down.
Symptoms:
Let’s start by looking at the common symptoms you may be experiencing as a result of too much clutter on your PC. By confirming the symptoms you can feel more assured that the treatment plan will be the correct one. Generally speaking we are comparing the performance when a PC is freshly installed and running to the overall responsiveness you now experience with your PC.
Typical symptoms include:
- Slow startup time.
- Slower times to open programs, save files, close programs, and perform regular operations.
- Computer freezes or locks up. This means that your PC does not respond or stalls as if waiting for you to do something. It can be more frequently experienced when more than one program is running at a time.
- Computer crashes or shuts down on its own.
Cause and Effect:
There are numerous causes that are contributing to poor performance as a result of PC clutter. Over time and daily use, PC’s get clogged with clutter and junk files clog up the system.
Most commonly experienced causes of “Too Much Junk”:
- Unwanted files get stored on your PC when you browse the Internet. Web browsers produce caches of files when you surf the net.
- Unwanted files get stored on your PC during downloads. Programs create Temp folders and files to temporarily use during an installation.
- Uninstalled remnants: Items are not always removed when uninstalling programs. This can happen even after you have successfully completed the un-installation of a program. These are sometimes referred to as “orphan” strings and files which are left in the registry and on the hard drive.
- Redundant programs can lead to excessive action behind the scene (taking up PC processing).
Surfing the net, getting files in email attachments, installing applications from the Internet… these are regular day-to-day activities. The result is fragmentation – files not stored in a contiguous manner. This can include having many interdependent files that make up a program stored further apart. These items become scattered across the hard drive which causes excessive movement of the hard drive and undo wear and tear. In the case when there are too many redundant applications running there can be processes that are actively competing for computer resources in the background.
Solutions – Clean & Uninstall:
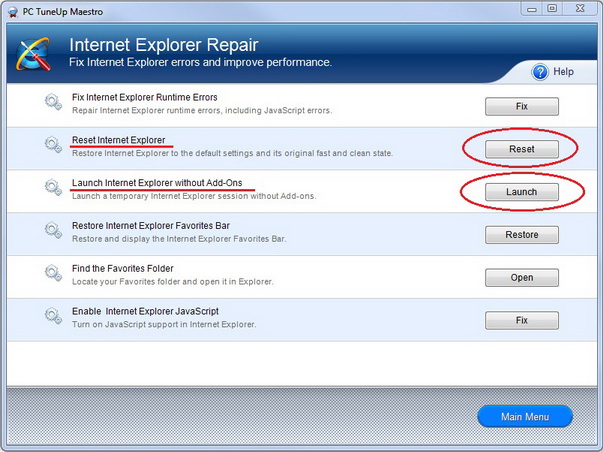
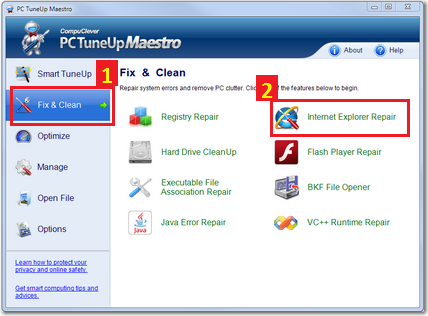
So what have we learned? Too much clutter of junk items can cause your PC to be slow in many ways. To be specific, the result of junk files and unnecessary programs is that these items take up disk space and can use available memory thereby resulting in slowdown and unexpected behaviours. Maybe the real question though is: how do you best remove these especially when considering that it is a task that you need to do periodically – it’s not a one-time fix. As we stated, having too many programs that can perform the same functions can also be detrimental. This is why PC Clean Maestro is so crucial to cleaning up and improving the PC state. Let’s take a closer look.
Clean:
There are junk items that are considered to be the “low hanging fruit”. That is, they are somewhat less challenging to locate and remove. They also, in this case, produce some pretty good results in terms of how much hard drive space is reclaimed as a result. Here is what we consider to be the top five items for removal.
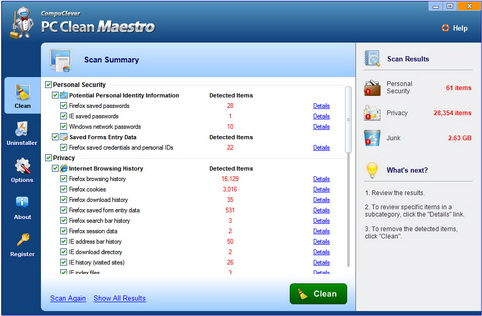
- Recycle bin items: If you are a fairly new PC user you may be unaware that when you delete items they get moved to the “Recycle bin”. The reason for this is that you have the option to reclaim them if you decide you were too hasty deleting them. However, these still take up hard drive space and the bin can get as full as you have available space on your PC.
- IE download files: Just surfing web pages leads to downloading of content including media files. This can add up over time and it needs to be flushed from your system on a periodic basis.
- Installer files: Cab files are downloaded to your system during an installation of programs that are sizeable. For example, Windows Office. A cab file (short for cabinet and seen as “.cab”), is a library of compressed files. They can be used to reduce the download size and time for web content required for an installation. Once an install is complete you no longer require these files. For some programs you may want to back these files up to an external hard disk to prevent having to re-download them.
- Windows Temp folder: Temporary folders are for storing temporary files. This is intended to be a temporary storage and some operating systems automatically delete the items with each reboot. Windows does not and you need to initiate this procedure. In some cases it is best to remove only items that are considered older than seven days.
- Windows cache files, dump files, and error reports: Windows automatically creates files and reports that are based on certain incidents for purposes of troubleshooting or re-simulation for analysis. These files can accumulate over time and are not relevant after the incident has passed (assuming it has been resolved).
PC Clean Maestro is designed to clean. All of these items we have mentioned, and more, can be detected and cleaned. After performing a quick scan a complete summary is provided and the total size of the junk items is tallied up. In some cases, this can add up to gigabytes of “junk” and can account for 5 -10% of your disk capacity.
Uninstaller:
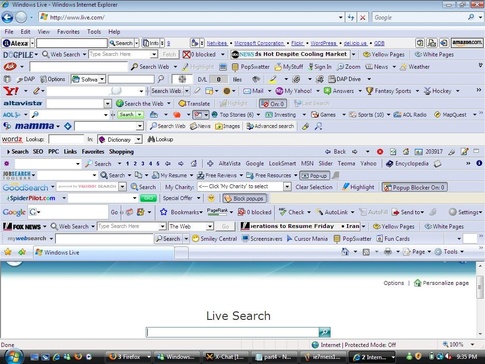
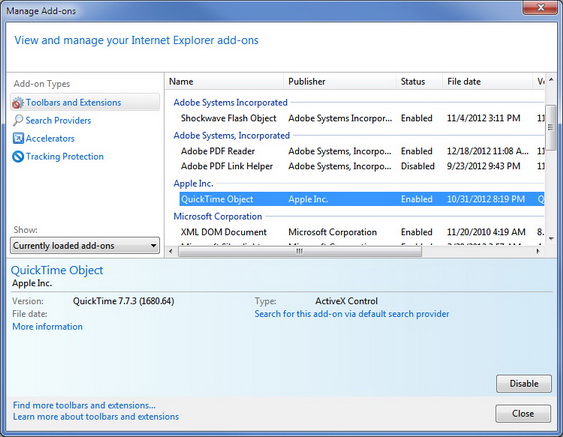
The Uninstaller tool in PC Clean Maestro is easy to use. Having this tool in the same program consolidates the clean process. Often times, applications are downloaded to your system when you are installing another program. This especially occurs when you are installing a program that is sponsored by a second manufacturer designed to appear on your browser toolbar or display popups prompting you to buy.
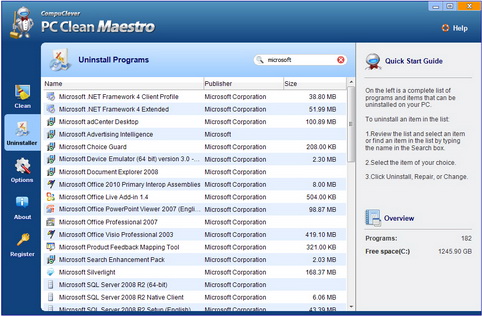
With the Uninstaller you get a complete list of installed items on your computer. You can select on any item from the list and, depending on how the item was designed, you are presented with being able to Uninstall, Repair, or Change. With the Change option you can modify the settings that you were first presented when you installed the program.
One of the more challenging questions facing every user ultimately is… how do I know what to uninstall? The basic answer is to resolve two questions: how is this application used on my PC and can I trust the manufacturers of this software. This can involve doing some online research. You can examine a program and verify that it is has gone through an authentication or certification process; type the program name and “certified” in a Google search and check the results. For more information, refer to our blog article: “The Clean and Uninstaller Tools”.
In Summary – Lean & Clean:
We’ve covered the basics to understanding the importance of cleaning your PC. We’ve introduced the tool to use: PC Clean Maestro. One important item to mention, users of PC Clean Maestro can use all the functionality presented here for free.
Tip: There are other functionalities to improve your PC computing experience relating to security and privacy which are included in the full version of the product. We hope to provide more information on this for you in an upcoming article.
Now that you are in the know about the benefits of keeping your PC lean and clean, we will provide some instruction on how to go about it in our blog article including how to use the Clean Scan Schedule tool. We hope the PC Clean Maestro operations will help you recapture the computing experience you once had when first operating your PC.

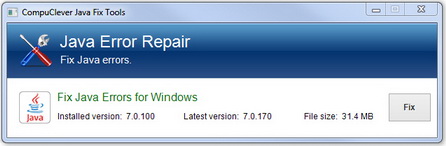
 In simple terms, Java is a programming language that is used to create software programs. In other words, it’s the underlying technology for business applications, games, PC utility tools, and more. As of 2012 it has been used for client-to-server web applications by over 10 million users. One reason for its popularity is that it is a simplified language that was designed to eliminate common programming errors. It was also designed for programmers to “write once, run anywhere” – that is, the code needs only to be written once to be able to run on computers with different operating platforms. Technically more than a programming language, Java is also a platform for developing applications. This means that programmers do not have to be concerned if the application is running on a Mac, PC, or Linux. If the Java components, also known as runtime environment, are available, it will run as expected.
In simple terms, Java is a programming language that is used to create software programs. In other words, it’s the underlying technology for business applications, games, PC utility tools, and more. As of 2012 it has been used for client-to-server web applications by over 10 million users. One reason for its popularity is that it is a simplified language that was designed to eliminate common programming errors. It was also designed for programmers to “write once, run anywhere” – that is, the code needs only to be written once to be able to run on computers with different operating platforms. Technically more than a programming language, Java is also a platform for developing applications. This means that programmers do not have to be concerned if the application is running on a Mac, PC, or Linux. If the Java components, also known as runtime environment, are available, it will run as expected. There are several potential causes for a slow browsing experience. The plan is to identify the symptoms and then to systematically go through potential causes. We will attempt to rule out the ones less likely to be crippling your IE browser experience but are potential culprits all the same.
There are several potential causes for a slow browsing experience. The plan is to identify the symptoms and then to systematically go through potential causes. We will attempt to rule out the ones less likely to be crippling your IE browser experience but are potential culprits all the same.