Popularity: Just how popular are eBooks? Amazon announced[1] that it sells more eBooks than traditional printed hardcover or paperbacks. In some cases authors are able to have their written work published in an eBook when they are unable to have it published to hard copy. There are even websites that are dedicated to cataloging and making eBooks available to the general public.
What are eBooks and eBook readers? Let’s take a step back and talk about some of the basic concepts and items you need to know. The term “eBook” comes from “electronic book” and can also be referred to as a digital book. It is in fact a book-length publication that has been digitized to be viewed on an eBook reader, the software that is installed on your computer device to view and read the eBook. This means that any previous or new publication can be found in an eBook form; although, of course, not all books have been, or could be, digitized. What’s more… some publications can only be found in eBook form and have not been hard-printed. There are commercially produced and distributed eBooks that are meant to be read on dedicated eBook readers. However free alternatives are readily available and even borrowing eBook items from the library is now possible.
We highly recommend that you try out the CompuClever application Ultra eBook Reader. There are numerous advantages including:
- You can easily open 12 of the most popular eBook formats.
- Multiple view layouts such as: single page, two page, and book view.
- Ability to bookmark, convert, and print your eBooks.
- Designed for your PC, laptop, or tablet.
Plus there is the added advantage of knowing the makers of the software are trustworthy and offer an outstanding support service. Check out: http://www.ultraebookreader.com/
The Devices: Mobile devices are in the hands of the many. eBooks can be read by more devices than just your PC. You can view them on your laptop, tablet, mobile phone, smartphone… you get the picture.
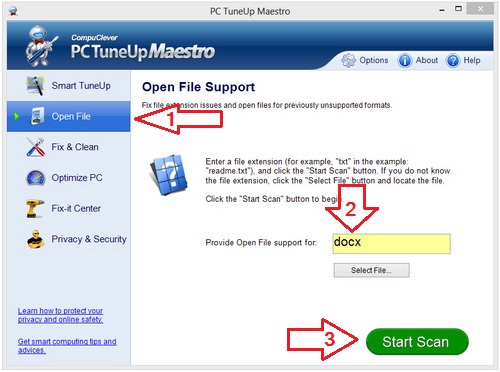
eBook Formats: Just as a Word doc has a particular format and a certain extension that signifies the the type of file it is (“.docx” for example), so too are there designated formats for eBooks. Leading the list of the many formats are: ePub, MOBI, PDF, AZW, LIT, and ODF. Some of these, like the Amazon format AZW, are exclusively used for the Amazon “Kindle” books. While we won’t go into the intricacies of eBook formats and the many formats available we will say that one item to be aware of is that some eBooks can be…
It is also useful for you to know the formats that are supported by your eBook reader. For a list of the formats supported by Ultra eBook Reader go to this page.
Advantages
There are numerous advantages to eBook reading. Here is our list:
- Space: Top of the list and perhaps tied with the number two item, is being able to save on space associated with hard copy books. Having books collect dust on a bookshelf is not an ideal situation. On top of this, finding an eBook on your PC or tablet is a lot easier than digging through boxes or trying to find it on a shelf. There are even advantages here when reading in bed or when in transit. With eBooks you are only limited by the capacity of your device and it’s quite feasible to have thousands of eBooks on hand.
- Mobility: If you are traveling, what could be easier? You can have thousands of eBooks at your finger tips and not take up any extra space or weight. You won’t have to pick just one book to travel with or have to worry about excess luggage weight and space. You can also read in dark places and in most any situation such as when waiting in line.
- Publication: Some publications go out of print while eBooks, once in electronic form, do not have any limitation with respect to copying and distribution. Also, you can get an eBook immediately rather than having to go to the library during specific hours, visit the bookstore, or wait for delivery.
- Cost: Many eBooks are free and there are other paid options as well. Scribd, one of the major players in document sharing and downloading companies actually offers a subscription based model with a monthly fee (much like Netflix), in exchange for unlimited access to all books they have for download. Of course there are some upfront costs but if you already have a laptop or tablet or mobile device, you will find that the electronic form is more affordable in many cases. As for free… all works of fiction from before the year 1900 are in the public domain and most libraries lend current eBook titles for limited times. The reality is, eBooks can be printed for less than the price of new hard copy books. For students, there is a very real potential to reduce education costs of publications and having the information in electronic form would be very useful when it comes to studying and writing papers.
- Reduced reliance of physical materials: Yes, you need to have a laptop of mobile device to begin. If you already have one then you are on your way to saving trees and the energy that goes into the making and distribution of books. This is especially relevant for more disposable publications such as magazines and newspaper. Imagine if these items were in electronic form for the most part and deleted rather than stacking up in landfills or recycle plants.
- Borrowing eBooks: As mentioned, libraries can lend out digital publications and this means having these items available with no restriction in terms of library hours. For students this is a major advantage.
- Loss or damage: eBooks can be replaced with little effort. Hard copy publications are susceptible to wear and tear, fading, water / fire damage, and of course dogs and small children with the single intent of shredding. Depending on the DRM (Digital Rights Management) policy, you may be able to backup your digital publication or even recover it without cost from the distributor.
DRM – Digital Rights Management
One important consideration to be aware of when acquiring eBooks is some are protected with a DRM wrapper. That is to say some formats can be protected by a digital rights management (DRM) anti-piracy tool which has been put in place by some publishers and copyright holders. While the intent is to protect “intellectual property” there are those that believe there is no evidence to support this and it simply inconveniences the legitimate customers.
Due to the controversial aspects of this technology, CompuClever has simply chosen to not support eBooks that come with a DRM wrapper. These items need to have the required authentication (think of it as a type of encryption). The good news is, there is a plethora of available eBooks that do not use a DRM wrapper and many of these are free.
Free eBooks
There are many eBook sites available and some offer free publications and others include both free and paid items. We have taken a look to see if these sites are legitimate according to a reliable website security scan (we use www.urlvoid.com). Here, in no particular order, is a list to get you started:
| eBook Sites |
|
| Gutenberg.org | This site has offers over 42,000 free eBooks and a link to 100,000 more free eBooks. You can “choose among free ePub books, free Kindle books, download them or read them online.” They also accept donations – one way to help with the effort of digitizing more books. |
| The Online Books Page | Hosted by the University of Pennsylvania library, this is a simple site that claims to list over 1 million free books. |
| Scribd | Scribd is the world’s largest digital library, where readers can discover books and written works of all kinds on the Web or any mobile device and publishers and authors can find a voracious audience for their work. |
| Kobobooks | This one also claims to have over 1 million free books. It also has copies for sale at reasonable rates. |
For those adventurous and keen readers check out this site, which provides 20 of the best websites to download free eBooks with screenshots and links.
We fully appreciate that hard copy books have a certain appeal and some people will not substitute them for a digital version. We also fully believe that real books will not simply disappear as a result of eBook popularity. It is our feeling that eBooks offer a viable alternative and can be used in conjunction with owning and reading actual books. We hope we have provided you some new insights about eBook reading. We will continue to introduce new technologies in a manner that is not beyond the reach of average, everyday computer users.

 So let’s begin by first examining the particulars.
So let’s begin by first examining the particulars.