
We’re going to start off with some information on clutter and how to assess how much free space you may have on your PC. Keep in mind that you may have plenty of free space and still have plenty of clutter on your PC. Assessing the situation can help in determining how your PC is performing and how well it responds to some clean up!
Clutter – Time to Clean
By “cleaning” we are not talking about throwing away things that may have some importance. We are referring to removing what can be considered clutter and organizing files we want to keep. By doing so we can not only improve the performance of the PC but make our lives a lot easier in terms of accessing the files and data we need.
Step 1: Assess
Assess space needs – how much free space do you have remaining. Most of us take pictures and movie files on our cameras and download them to our computer. These add up over time and need to be stored in a safe place (or at least duplicated to your external hard drive in the event you do have sufficient space).
To assess the file space needs you can do the following:
1. Open the Start menu and select Computer. (Some Windows OS systems label this “My Computer” and with Windows 8 you have to type: “this PC” when on the Start screen and select “This PC” from the search results.)
2. Locate your hard drive. This is Local Disk (C:) or Windows (C:) for most computers.
3. View the free space that is displayed for the drive. Tip: you can also right click on the drive and select Properties to see a pie chart of the used and free space.
For most computers there is typically a large amount of storage for your files and you may have a lot of free space available. If you still feel that it has been a while since you have removed unwanted files and, maybe, you feel that your PC is a bit sluggish in some ways.
• Slow startup time.
• Slower times to open programs, save files, close programs, and perform regular operations.
• Computer freezes or locks up. This means that your PC does not respond or stalls as if waiting for you to do something. It can be more frequently experienced when more than one program is running at a time.
• Computer crashes or shuts down on its own.
• Redundant programs can lead to excessive action behind the scene (taking up PC processing).
If your feel any of this applies to you and you want to take advantage of a clean PC system, we highly recommended removing clutter from your PC.
Step 2: Backup
Begin by backing up and organizing files (media files especially) that need to be put on to an external hard drive. This article deals with removal – permanent removal – of unwanted items. The key is “unwanted”. We strongly recommend that you make a copy of all files that are important to you. The price of external hard drives makes this a no-brainer and hard drives available these days are often more space than what the average person needs – some are now terabyte in size (1,000 GBs). The added advantage of having a good backup and storage strategy is that you are working toward optimizing free space on your PC.
Step 3: Deal With the Junk:
There are files that get onto your computer without us even knowing how they got there. Here’s how they likely got there:
- Unwanted files get stored on your PC when you browse the Internet. Web browsers produce caches of files when you surf the net.
- Unwanted files get stored on your PC during downloads. Programs create Temp folders and files to temporarily use during an installation.
- Remnants remain when you uninstall. Items are not always removed when uninstalling programs. This can happen even after you have successfully completed the un-installation of a program. These are sometimes referred to as “orphan” strings and files which are left in the registry and on the hard drive.
- Getting files in email attachments and installing applications from the Internet. Some of these become outdated or are not put into use.
These unwanted items build up from regular day-to-day activities. The result of too many junk files and unnecessary programs is that these items take up disk space and can use available memory thereby resulting in PC slowdown and unexpected behaviours. Maybe the real question though is: how do you best remove these especially when considering that it is a task that you need to do periodically – it’s not a one-time fix.
Use the Right Tool
We are looking at simplifying the process by using automated tools that do the job quickly and efficiently. PC Clean Maestro is designed to clean and remove unwanted items such as recycle bin items, temporary Internet download files, items in the Windows Temp folder, and other cache and system files. All of these items and more can be scanned and cleaned. After performing a quick scan a complete summary is provided and the total size of the junk items is tallied up. In some cases, this can add up to gigabytes of “junk” and can account for 5 -10% of your disk capacity.
With PC Clean Maestro (the free functionality of PC Clean Maestro) you can remove junk files and uninstall programs so as to free up space. By doing so you clear up PC clutter which can bog down the system and lead to poor system performance. Some best practices are provided so that your experience can be simplified and more trouble-free.
The Instructions: There are three areas of cleaning that can take place using the Clean Tool. We are staying focused on the free aspects of PC Clean Maestro. The following instructions detail how to remove Junk files from your PC.
- First you need to open the program. The window will appear as seen here:
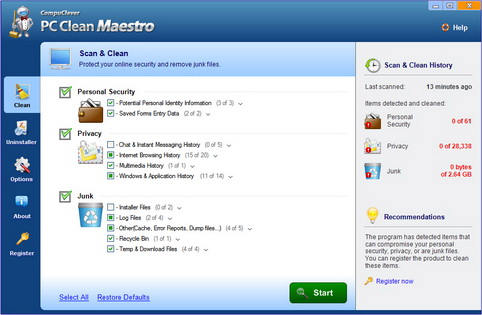
- Select items to clean. We are going to focus on Junk items only so clear the checkboxes for Personal Security and Privacy. You can then review and select any of the items in the Junk section (Installer Files, Log Files, Temp Files, etc.).
Note: You can refer to the help file for instructions on how to display all the individual items that are categorized. You can also get information on the three state check box system. - Initiate the scan using the “Start” button.
- Review and Clean. A summary of the scan is displayed including the number of detected items found in each category, the size that can be reclaimed, and a “Details” link. The link will provide the complete list of items found and the location of each item. You can clear any selected items before moving on to the next step.
- Clean. Click the “Clean” button to permanently delete these junk items.
Best Practices:
Create an automated schedule. Use the Options button in the Main window and select the Clean Scan Schedule. From here you can configure when you want an automated scheduled scan to run.
In Summary – Lean & Clean:
We’ve covered the basics of cleaning your PC and we’ve introduced one aspect of PC Clean Maestro. It’s also great to know that anyone can use all the functionality presented here for free. There are many other features relating to security and privacy that are available for registered users and we will provide steps and tips on how to use these in our articles.
We hope this article has helped gain some insight and offered you some effective strategies on cleaning your PC. We will continue to provide story lines like this that benefit all of us and we will describe them in a manner that is within reach of everyday computer users. If you have some ideas of topics you would like us to cover, email us at: newsletter@compuclever.com

 On Jan 30th Yahoo, the second largest email provider with 273 million accounts, confirmed an attack and announced that malicious computer software was able to access a list of Yahoo Mail accounts’ usernames and passwords. Although details were not provided they point the finger at a third-party database compromise. The statement was made:
On Jan 30th Yahoo, the second largest email provider with 273 million accounts, confirmed an attack and announced that malicious computer software was able to access a list of Yahoo Mail accounts’ usernames and passwords. Although details were not provided they point the finger at a third-party database compromise. The statement was made:
