In our Part 1 article we covered news related to the Facebook privacy scandal. In Part 2, we will emphasize what you can do. We’ll provided three best-practice recommendation for protecting your identity and privacy.
Our Private Data
As Facebook users we accept the privacy policies when we sign on. For the most part we don’t even read over the extensive policy pages. Instead we set up our account and enter data related to our personal lives. We understand in the process this information gets recorded and stored.
Take Action:
We recommend that you get a clear idea of how much and what kind of data Facebook collects on you. Check out the “Data In” section of our previous article for directions on accessing the data Facebook has collected from you.
Facebook is a free service and we can expect that they make revenue by providing our data to advertisers. What many of us are not aware of is that they pass on our data to third party developers and organizations.
This is why we can sign on to a new app or online service using our Facebook login. Right away they can access our data so that it is easier for us to create a new account with the third party app rather than having to enter all the personal information they require once again.
But what kinds of control are in place once our data leaves the hands of Facebook? What kind of regulations are there to protect our privacy and information? This is what Facebook’s Mark Zuckerberg has to address.
Facebook Updates
In the past Facebook has revised its privacy policies. However, these previous revisions have been toward openness and sharing rather than protection of privacy. Unfortunately, “…they were optimizing for profitability rather than security and privacy of their members” says David Kirkpatrick author of the Facebook Effect.[1]
Zuckerberg’s promise at the beginning of this year was to fix Facebook in 2018 – this is no small task. In fact, he has stated that fixing the company’s problems will take years.
Presently, users are informing users in their News Feed if they’re among the millions of people whose data was improperly harvested by Cambridge Analytica.
Other changes we can expect in the near future: [2]
- Users will receive notice of all apps they use and what data is shared with those apps. They then have a chance to delete apps they no longer want.
- Facebook will restrict access to certain data that applications can acquire.
- The option to search for users by entering a phone number or an email address will be removed.
- Facebook will set out to delete all logs after a year and only time of calls will be collected.
- New policy will also make users aware that WhatsApp and Instagram are part of Facebook and that the companies share information about users. WhatsApp will still have a separate policy while Facebook and Instagram continue to share one.
Free
Whenever something is offered for free we need to ask: how is this business generating revenue? Some companies offer a trial license for their software as a means to test drive the service. Others rely on donation.
In the case of Facebook, it is free to users but there are associated costs. Not only does Facebook sell data to advertisers who then place ads that are targeted to meet our purchasing preferences, they also harvests our data for app developers as well.
Surveillance Capitalism:
One term being used in many news sources related to this Facebook scandal is “surveillance capitalism”. Shoshana Zuboff, Harvard Business School professor states that it drives much of the internet.
It’s behind most of the “free” services, and many of the paid ones as well. It utilizes psychological manipulation in the form of personalized advertising to persuade you to buy something or do something, like vote for a candidate.
“…while Facebook is one of the biggest players in this space, there are thousands of other companies that spy on and manipulate us for profit.” [3]
We need lawmakers to force these companies into the public spotlight and to enforce lawful conduct.
Regulation
Although Facebook is in the process of change and updates we need to ask: how is it possible to keep private data secure after it’s sold to third parties? Facebook has admitted that it is impossible to monitor what these third parties do with the data once it is out of their hands. However, Mark Zuckerberg has said that his industry should be regulated.
At present he is facing Congress and has delivered an apology and is answering questions. But what will be the outcome of this? What about past regulation? Zuckerberg has stated they regularly testify before Congress on a number of topics.
In 2011, Facebook offered privacy assurances in a settlement with the FTC (Federal Trade Commission). Allowing Cambridge Analytica to harvest data could be a violation of that settlement. The ability to transfer the data of users’ friends should have been banned with the 2011 consent. But what is the FTC going to do to enforce existing regulations?
Turning Up The Heat:
In 2016, the European Union passed the comprehensive General Data Protection Regulation, or GDPR. One mandate restricts collection of personal data of EU citizens to be only saved for “specific, explicit, and legitimate purposes” and only with user consent.
This means, consent cannot be buried in the terms and conditions.
This law will take effect in May and companies worldwide are paying attention. It is expected that this will expose the industry like nothing else. In preparation for this law, PayPal published a list of companies it might share your personal data with – over 600 companies.
Best Practices – Privacy at Stake
There is no doubt that privacy of information is at stake.
It’s essential that we throttle back on what information we make available online and what data is stored on our PC. Here are our recommendations.
-
- We recommend the privacy functionality associated with PC Cleaner. By using the available functionality you can see all the personal and private data you have on your PC which could be accessed by illegitimate means.
-
- When on a public Wi-Fi network, we highly recommend not sharing out any sensitive data. Even downloading records online from a public location or terminal can leave your data vulnerable to hacks.
- If you decide to delete your Facebook account, consider the following:
- You will need to sever all ties with Facebook including Messenger, WhatsApp, and Instagram. Your data can be shared with these apps and policies are similar or, as with Facebook and Instagram, shared.
- Any apps that you “log in using Facebook“ will no longer work and you will have to enter your log in credentials for these.
- Delete all Facebook instances from all devices including your mobile ones. Make sure you delete and not deactivate. Use this link from Facebook.
- Do not even attempt to log in to Facebook for at least two weeks or you will cancel the account deletion process.
Last Comment
We started out this two part series asking a question of what to do as a Facebook user. Undoubtedly, the data breach has been the final straw for some and these users are choosing to delete.
Do we throw the baby out with the bath water?
We need to acknowledge that there are positive online developments, and we need to take an active role in shaping it.
With respect to the baby / bath water analogy – we certainly can agree the bath water is dirty!
As for the baby – in the case of social media technology – we need to closely examine if it’s being overfed.
“…the thing we need to understand now,” Shoshana Zuboff states, “is that the online world, which used to be our world, is now where capitalism is developing in new ways.”
[1] http://money.cnn.com/2018/04/09/technology/

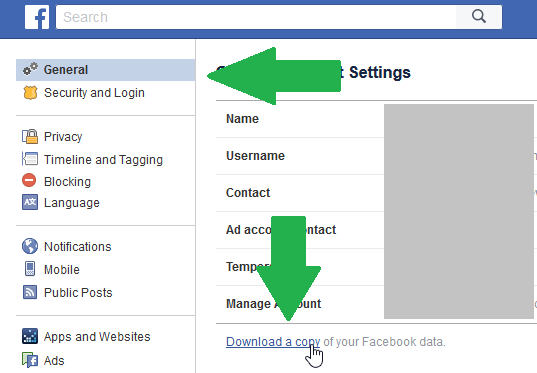 To download your information:
To download your information:
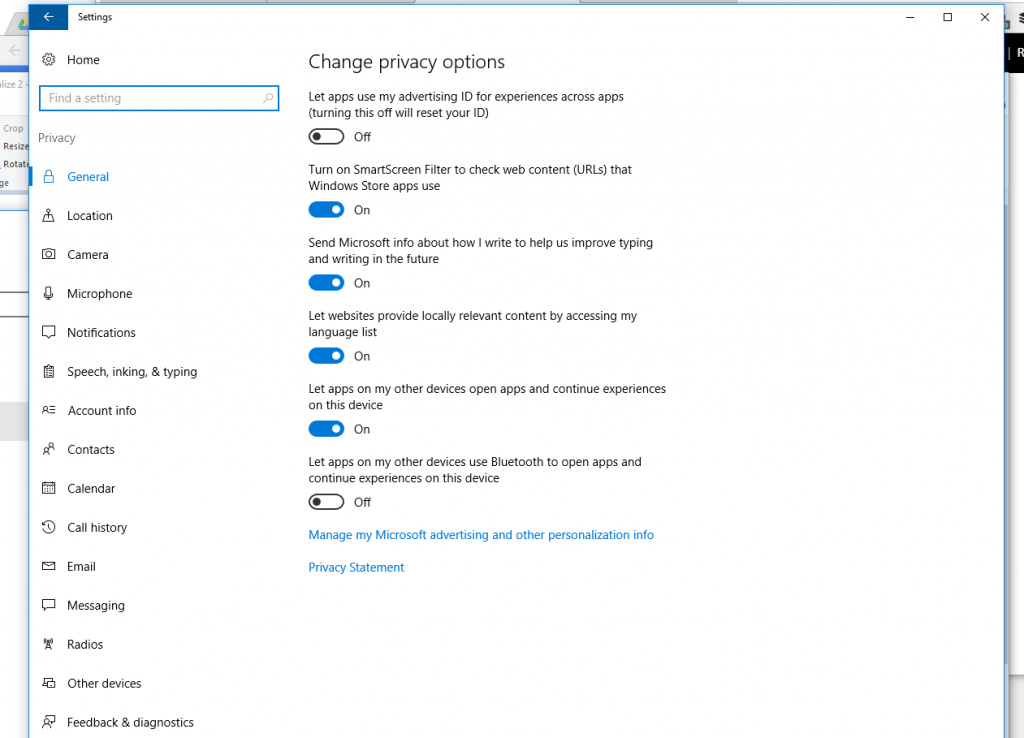
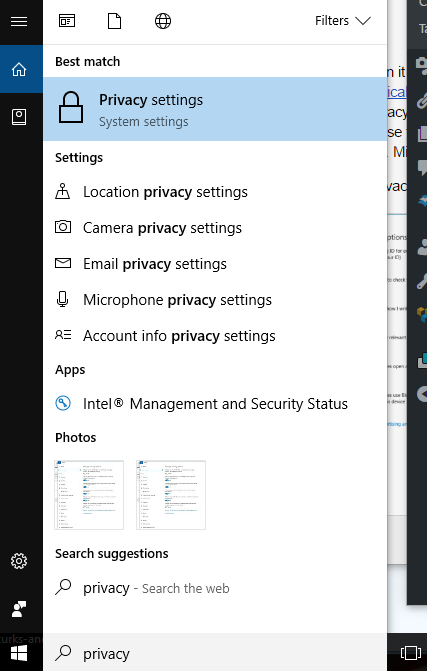 Next, type in “privacy” in the search box.
Next, type in “privacy” in the search box.