Introducing – PC Clean Maestro:
Introducing – PC Clean Maestro:
The CompuClever application PC Clean Maestro has more than one major function. It is used to remove junk files, to uninstall programs, and for removal of data for purposes of security and retaining PC privacy. Removing private data that is sensitive or can be stolen is done in the same manner as removing junk files with minor differences. We will outline the procedure here in step-by-step fashion. Before we begin, let’s start with a best practice tip.
Best Practices: 1. BackUp Data
As we stated in our previous article… backup your data! This article deals with removal – permanent removal – of sensitive and private items. As can be seen in the list provided below, these are items that are automatically created by ongoing functions of your PC including passwords, personal credentials and ID’s that you have entered when online.
It is good practice to make a copy of all files that are important to you and safer practice to keep these stored on an external hard drive. Today’s hard drives are often more gigabytes than the average person needs – and some are now terabyte in size (1,000 GBs). External hard drives prices are very reasonable and there the added advantage of having a good backup and storage strategy is that you are working toward optimizing free space on your PC so that it can run faster.
Best Practices: 2. Configure Your Browser Privacy
You can configure your browser settings to better restrict the privacy controls. Refer to your browser settings and look for “privacy” or “security” (or both). By configuring these settings you choose what items to block or restrict including cookies and Private browsing or Do Not Track (DNT) browsing traffic. In recent years all major browsers have included a Do Not Track (DNT) option. This enables a user to choose to not have their online activities tracked. This applies to Internet Explorer, Google Chrome, Mozilla Firefox, Safari, and Opera. The one shortcoming of this: “The Do Not Track system is completely voluntary, and there are no legal or technological requirements for its use. As such, not all websites and advertisers will honor the request or may completely ignore it altogether.”[1]
The Personal Security and Privacy Scan
By using PC Clean Maestro you can detect personal data items that are automatically stored on your PC. Any of these items on their own may not constitute a substantial threat. However, these items together – personal addresses, passwords, account information, and more – can be used together to provide an intruder what they need to gain access to perform financial transactions or use your data unlawfully. Here is a summary of the items that PC Clean Maestro scans:
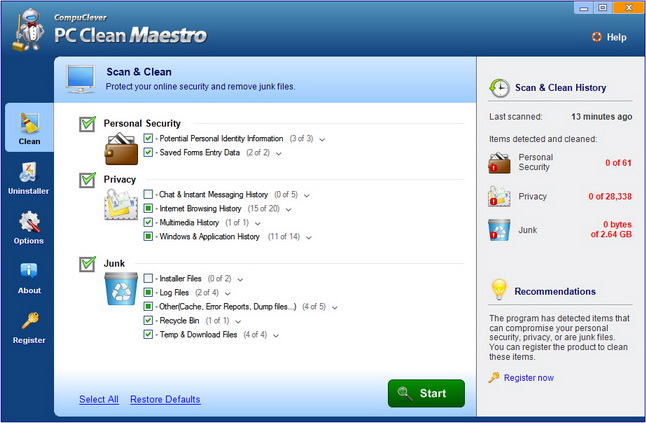
Personal Security
- Personal Identity Information: IDs and passwords used for Windows and for Internet access.
- Saved Forms Entry Data: name, address, phone number, credit card information.
Privacy
- Chat & Instant Messaging History: Skype and Windows Messenger messaging content.
- Internet Browsing History: visited URLs, downloads, search history, cached images.
- Multimedia History: videos watched.
- Windows & Application History: Windows clipboard, document history, applications used.
The Steps:
There are three areas of cleaning using the Clean Tool. We are staying focused on the privacy and security aspects of PC Clean Maestro. The following instructions detail how to remove items that are a threat to personal security and privacy.
Step 1: First you need to open the program. The window will appear similar to as seen below. We have expanded the Personal Security and Privacy sub-item sections to get a closer look at the items listed.
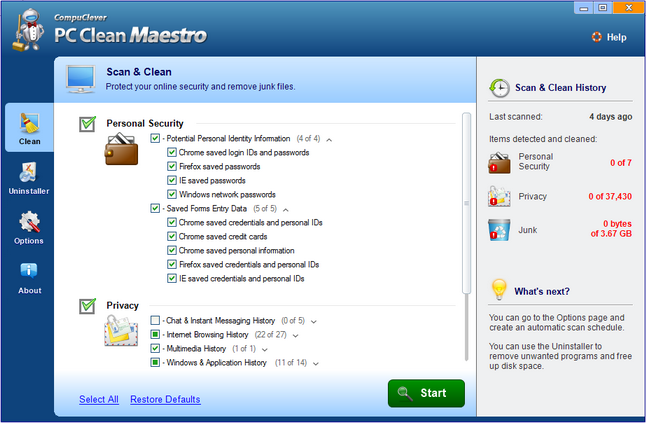
Step 2: Select items to scan. Of the check boxes available you can review and clear items you want to remain on your PC.
Step 3: Initiate the scan using the “Start” button.
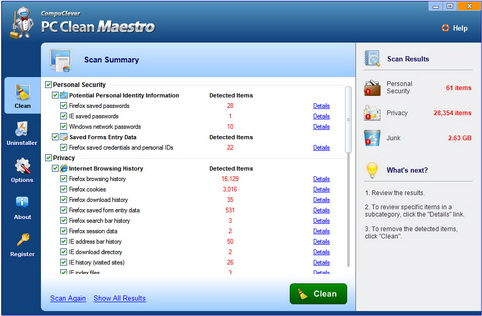
Step 4: Review and Clean. A summary of the scan is displayed including the number of detected items found in each category, the size that can be reclaimed, and a “Details” link. The link will provide the complete list of items found and the location of each item. You can clear any selected items before moving on to the next step.
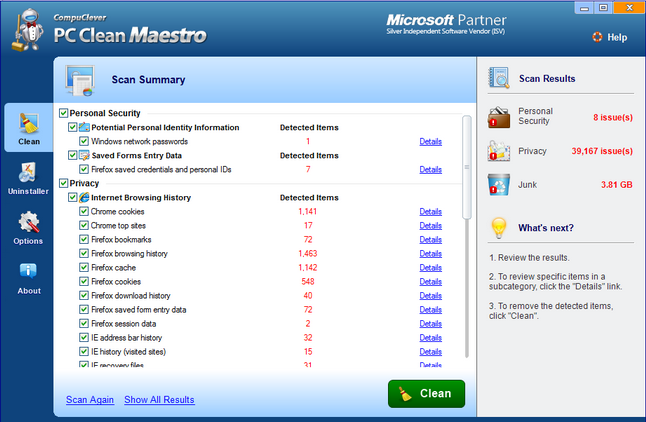
Step 5: Clean. Click the “Clean” button to permanently delete the selected items.
Best Practices: 3. Regular Use of PC Clean Maestro
Create an automated schedule. Use the Options button in the Main window and select the Clean Scan Schedule. From here you can configure when you want an automated scheduled scan to run.
Question Period:
What browsers do you support?
We support Google Chrome, Mozilla Firefox, and Windows Internet Explorer. We also support the cleanup of history information recorded by Skype, Adobe Flash Player, Microsoft Excel, Power Point, Microsoft Word and several Windows items.
What are cookies? Do I need to remove them?
Web cookies are used to identify you and prepare customized web pages. Here is an example: you do online banking and it involves entering your account and password. When you do a cookie is created that will store the account information so that when you next visit the site you only have to press the first letter or number of your account and it displays the rest. This is pretty handy right? This is where you have to decide if the convenience is worth the potential risk of having your account information passed on to someone who can access your PC without your knowledge or approval.
How often do I need to clean personal and private data?
Much of this depends on how often you perform certain functions on your PC. For example, when you do online banking a cookie is created when one is absent (even though you removed it from the previous session). You can look into not having your browser store web cookies but this is only one aspect of what you may want removed from your PC. Regular removal of your browser cache is good practice – it maintains your privacy and frees up space. Browser caches and a history of your online activities are automatically stored by your web browser.
Best Practices: 4. Staying on Guard
- Take note of drastic changes to your PC! If there is a malicious item that has infected your PC, chances are it will alter the functioning of your PC. Make sure your vital financial information is not accessible as stated in this article. Next, consider using a trusted anti-malware application that can scan and remove the intrusion.
- Be aware of suspicious emails and phone calls. Here are two examples:
- An email arrives in your mailbox saying that your PayPal has been suspended (or your credit card is blocked). The email looks very authenticate. The same font and colors that PayPal uses on their website. The email uses your email address in the “From” column. The email goes on to instruct you to click a link to activate your account.What do you do? Not getting an actual email address from the trusted company is your first clue that something isn’t quite right. An informed PC user will hover the mouse cursor over the link and look in the bottom of the window (the status bar) to see if the link that is displayed is in fact one belonging to PayPal. To verify this is a potential hack or scam of some kind, you can also right-click the link – being very careful to not actually left-mouse click and get taken directly to a web page that may download unwanted items to your PC. So… you carefully, right-click the link and select “Copy Link Location”. You can now open your browser and check the validity of the URL by going to a site like URLVoid. Simply paste the link and submit it for verification. Even if it does come up clean… you can always go to the source. Contact the trusted company and give them the details. In this case… they will ask you to forward the emails so they can follow up with this spoof.
- You get a phone call (with no phone ID displayed) and someone says they are from “Windows” and states they have detected that there is a virus on your computer. They immediately ask you if you are by your computer and if you can follow some instructions. You are directed to go to a web site and run some tests. What do you do?You do not have to follow their instructions if you do not trust who is on the other end of the phone. Ask for verification of who they are. Ask how they obtained your phone number. Ask them for their name and phone number so that you can call them back. You will find that the phone call will end quickly by them and you have protected your personal data and the integrity of your PC.
Keeping your PC safe requires a bit of effort and a whole lot of vigilance. Hackers are like predators – they will prey on the weak. In this case the weak are the uninformed. We hope this has helped you gain an upper hand in defending your PC safety.
Reference

 Cybercrime has been a growing concern since the onset of the first computer virus. The very first PC threats were more about status and cyber geeks flexing their brain muscle as they penetrate computer defenses and proliferate in typical virus fashion. These days there is much more to lose. Personal information and finances can be stolen with the use of more sophisticated and stealthy technology. One recent hot topics in this field is “skimming wallets” – theft which involves just walking past someone and picking up there credit card information. We will look at this and other forms of cybercrime and speak to how to guard yourself from PC cyber attacks.
Cybercrime has been a growing concern since the onset of the first computer virus. The very first PC threats were more about status and cyber geeks flexing their brain muscle as they penetrate computer defenses and proliferate in typical virus fashion. These days there is much more to lose. Personal information and finances can be stolen with the use of more sophisticated and stealthy technology. One recent hot topics in this field is “skimming wallets” – theft which involves just walking past someone and picking up there credit card information. We will look at this and other forms of cybercrime and speak to how to guard yourself from PC cyber attacks.