Even Microsoft makes the point:
Well… if your PC is suffering from too many installations it’s time for some startup management. Keep in mind that with many applications you install today – especially free ones – there are most likely add-ons that come with the program. Add-ons are bundled together with the application you want but you do not need to install the entire bundle.
Let’s Get Started!
We are going to be using free functionality available in PC TuneUp Maestro. The Startup Management feature provides access to the applications that launch when you boot your system so you can optimize your computer’s startup performance. From the list that is provided you can enable or disable items and you can also choose to remove items from the list entirely.
The steps include: Opening the Startup Manager; reviewing the items in the list; and then Enable, Disable, or Remove.
1. Open Startup Management:
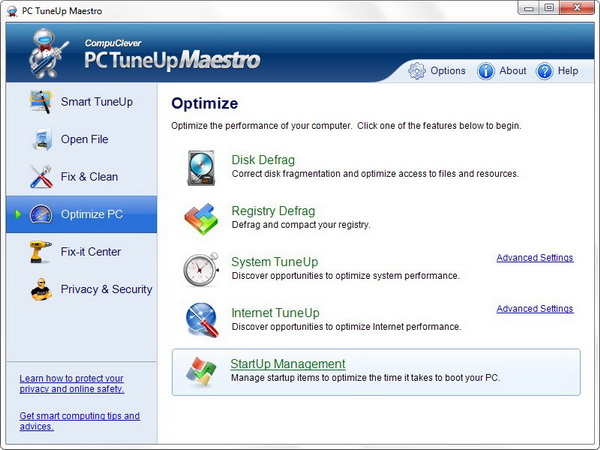
Begin by opening PCTuneUp Maestro and go to the “Optimize PC” page as seen in the screen below:
Next, click the StartUp Management link.
2. Review:
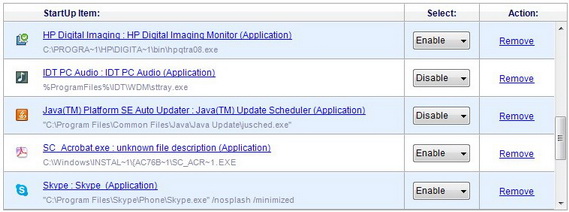
There is a list that is provided with all the applications that are launched during the startup process. The items that appear in the list will look like this screenshot:
You can review any items in the list to make an informed decision about how to best manage each. This is especially advisable with ones you are not familiar with.
To review a startup application in the list, click the blue link associated with the item.
3. Disable and Remove Options:
From the Startup list, you can check the status of any item in the Select column. If it is marked as “Disable” then it does not launch when you start the computer – no need to worry.
- Disable: If something in the list is marked as “Enable” you can click the drop down arrow next to it and select: Disable. The item remains in the list and no longer starts when you boot your computer.
- Remove: You also have the option to remove the item altogether but you will see a warning dialog warning you that you cannot use the program to restore it. This removes the item from the Startup list but does NOT delete or uninstall the application.
Other Troubleshooting Tips:
If you are still experiencing problems you may need to dig a little deeper. There are other tools available with PC TuneUp Maestro that can improve the situation. Here is what we suggest:
- System TuneUp: Try the System TuneUp function provided from the Smart TuneUp section (top of the navigation bar). Make sure the System TuneUp option is checked and then click Start. There are items that may come up to improve not only the StartUp time but also ShutDown and system speed.
- Registry repair: You can clean and defrag your registry as well. This can often times result in performance gains. The registry functions are also found in the Smart TuneUp section. Make sure the “Registry Repair” and “Registry Defrag” options are checked and then click Start.
- Defragment the hard drive: A poorly performing hard drive can also aggravate the situation with respect to the PC boot speed. We suggest cleaning any junk files and performing a defragmentation. Check out our article: How to defrag your hard drives.
In Summary:
We’ve looked at one aspect of PC performance – Startup Management. This article comes at a good time as we get ready to roll out a new updated Startup Manager that will be released this fall. The features include:
- Providing time measurements for each startup program.
- Categorizing startup applications, startup services, and processes. The option to enable, disable, and remove applications from the startup process is provided as described in this article.
- Providing safety ratings and assessments for startup programs. Users are warned of dangerous or unwanted program that they should disable and remove from the Startup list.
We hope this article has helped gain some insight and offered you some effective strategies on cleaning your PC. We will continue to provide story lines like this that benefit all of us and we will describe them in a manner that is within reach of everyday computer users. If you have some ideas of topics you would like us to cover, email us at: newsletter@compuclever.com